Qi Li, Long Li, Wei Wang, Pengbo Nan. Image Inpainting of Damaged Textiles Based on Improved Criminisi Algorithm[J]. Laser & Optoelectronics Progress, 2023, 60(16): 1610011
Search by keywords or author
- Laser & Optoelectronics Progress
- Vol. 60, Issue 16, 1610011 (2023)

Fig. 1. Description of Criminisi algorithm
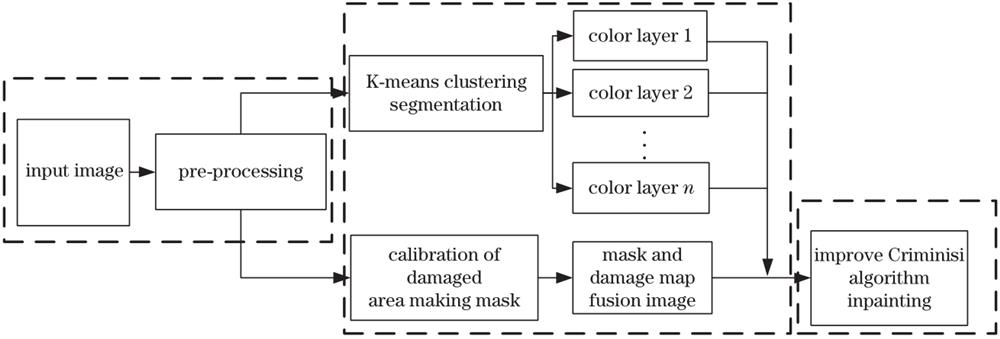
Fig. 2. Algorithm block diagram of textile cultural relic image restoration
Fig. 3. Boundary tracking results after denoising. (a) Raw wool fabric image; (b) boundary tracking images without denoising; (c) boundary tracking image processed by adaptive filtering; (d) boundary tracking image processed by proposed algorithm
Fig. 4. Schematic diagram of mask making process. (a) Original image; (b) damaged area; (c) mask map; (d) image to be repaired
Fig. 5. The result of K-means color segmentation
Fig. 6. Color dispersion of different pixel blocks. (a) Sample 1,
Fig. 7. Comparison of inpainting results of damaged textile cultural relics images by four algorithms. (a) Image of damaged textile artifacts; (b) mask map; (c) inpainting image by Criminisi algorithm;(d) inpainting image by reference [16] algorithm; (e) inpainting image by reference [22] algorithm; (f) inpainting image by proposed algorithm
Fig. 8. Comparison of repairing effect of artificial fictitious damaged textile image. (a) Image of original textile; (b) artificial virtual damage image; (c) inpainting image by Criminisi algorithm;(d) inpainting image by reference [16] algorithm; (e) inpainting image by reference [22] algorithm; (f) inpainting image by proposed algorithm
Fig. 9. Comparison of inpainting effects. (a) Original image; (b) damaged image; (c) inpainting image by reference [16] algorithm; (d) inpainting image by reference [22] algorithm; (e) inpainting image by proposed algorithm
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Table 1. Comparison of quality evaluation parameters (test 1)
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Table 2. Comparison of quality evaluation parameters (test 2)

Set citation alerts for the article
Please enter your email address



