Tianlun Li, Wenjun Xu, Yonggang Su, Shuaiqi Liu, Jie Zhao. Optical Double-Image Encryption Based on Fingerprint Key[J]. Laser & Optoelectronics Progress, 2023, 60(2): 0210015
Search by keywords or author
- Laser & Optoelectronics Progress
- Vol. 60, Issue 2, 0210015 (2023)
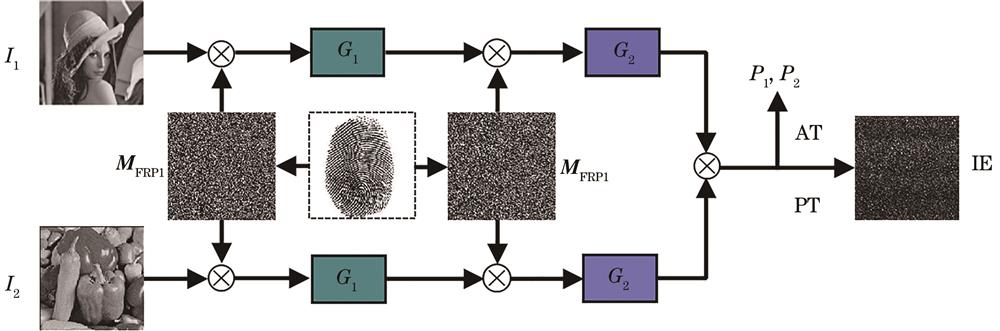
Fig. 1. Schematic of the encryption process

Fig. 2. Schematic of the decryption process
Fig. 3. Two original images and their encryption and decryption results. (a) (b) Original images Lena and Peppers; (c) fingerprint; (d)
Fig. 4. Decrypted results of image Lena with incorrect keys. (a) Incorrect fingerprint; (b) decrypted result with the incorrect fingerprint; (c)-(f) decrypted results with the incorrect parameters of the chaotic map
Fig. 5. Decrypted results of image Peppers with incorrect keys. (a) Incorrect fingerprint; (b) decrypted result with the incorrect fingerprint; (c)-(f) decrypted results with the incorrect parameters of the chaotic map
Fig. 6. Histograms of the original image and encrypted image. (a) Original image Lena; (b) histogram of Lena; (c) original image Peppers; (d) histogram of Peppers; (e) encrypted image; (f) histogram of the encrypted image
Fig. 7. Encrypted images with different occlusion sizes. (a)-(d) Occlusion size is 12.5%, 25%, 37.5%, 50% respectively
Fig. 8. PSNR and CC curves of decrypted images versus different occlusion sizes. (a) Lena; (b) Peppers
Fig. 9. PSNR and CC curves of decrypted images versus different intensity of Gaussian noise. (a) Lena; (b) Peppers
|
Table 1. PSNR of ciphertext images and original images
|
Table 2. SSIM of original images and decrypted images
| |||||||||||||||||||||||||||||||
Table 3. Correlation coefficients of adjacent pixels in original and encrypted images

Set citation alerts for the article
Please enter your email address



