Yi-Feng Li, Zhi-Ang Hu, Jia-Wei Gao, Yi-Sheng Zhang, Peng-Fei Li, Hai-Zhou Du. Efficient anomaly detection method for offshore wind turbines[J]. Journal of Electronic Science and Technology, 2024, 22(4): 100285
Search by keywords or author
- Journal of Electronic Science and Technology
- Vol. 22, Issue 4, 100285 (2024)
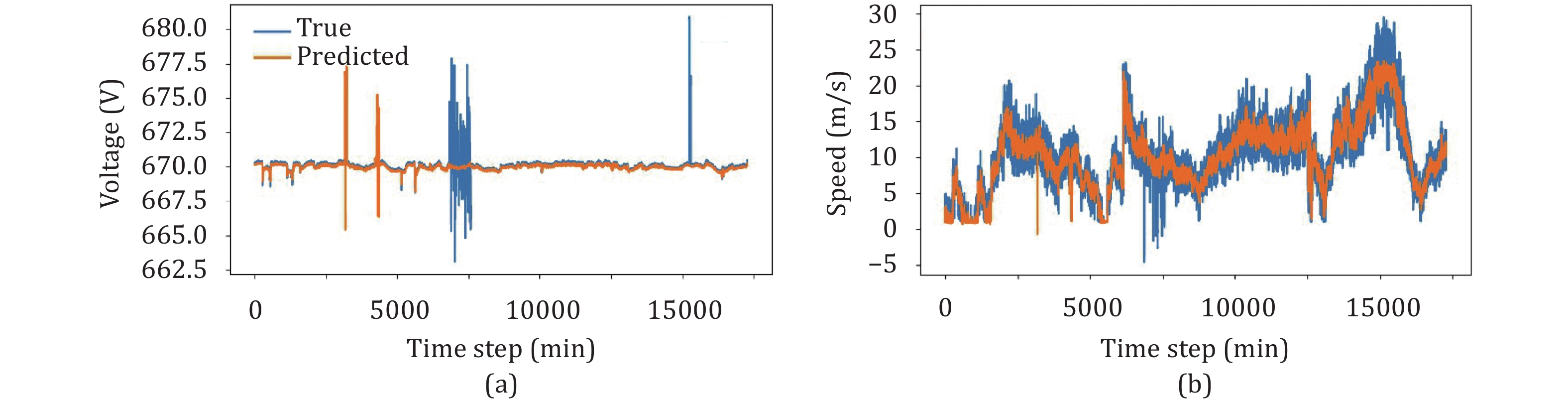
Fig. 1. Two examples on the real-world offshore wind turbine operational dataset: (a) contrastive of L1L2 line voltage and (b) contrastive of wind speed (mechanical).
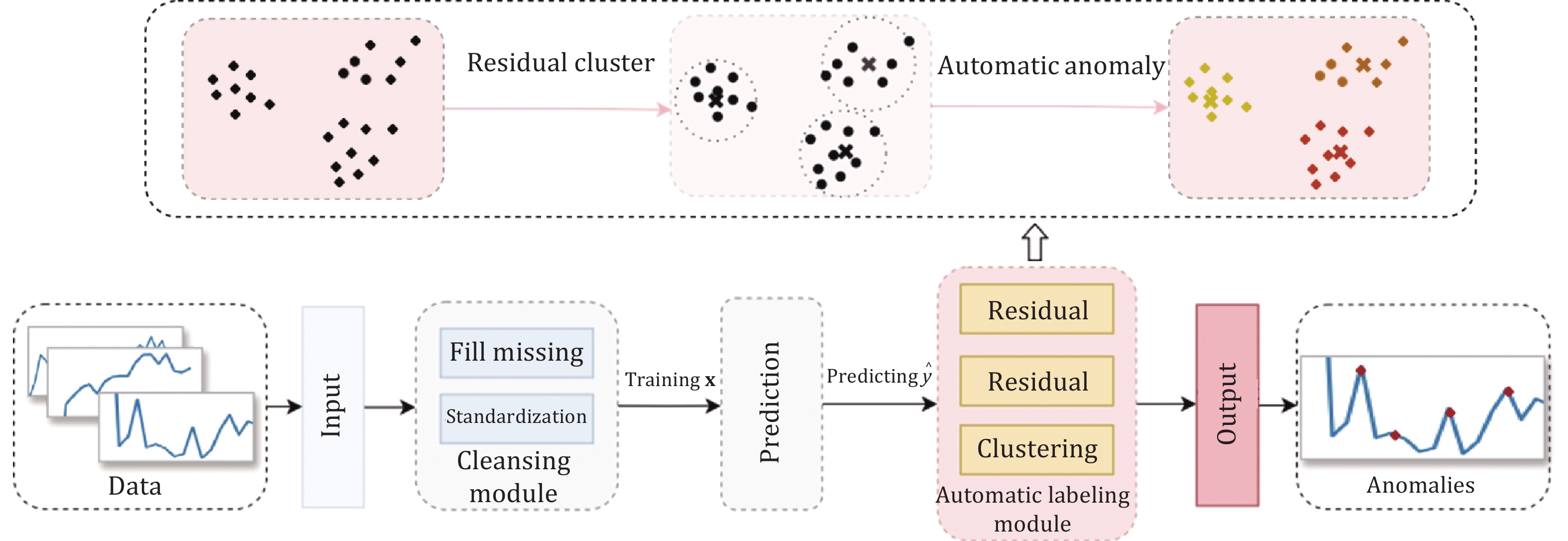
Fig. 2. Architecture of Hawkeye.
Fig. 3. Difference between DSW embedding and conventional embedding approaches. DSW uses episodes of different features to predict different episodes of data with different features. While the conventional embedding approach uses all the features in the same time episode for embedding and does not take into account the correlation between the multivariate variables.
Fig. 4. Two-stage attention mechanism.
Fig. 5. Comparison of (a) multi-headed self-attention mechanism and (b) our proposed router approach.
Fig. 6. Comparison of parameter file sizes.
Fig. 7. Anomaly detection results shown on two features: (a) L1L2 line voltage and (b) wind speed (mechanical).
|
Table 1. Datasets description.
|
Table 1. [in Chinese]
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||
Table 2. Performance on labeled public datasets.
|
Table 3. Anomaly detection results on an offshore wind turbine dataset.

Set citation alerts for the article
Please enter your email address



