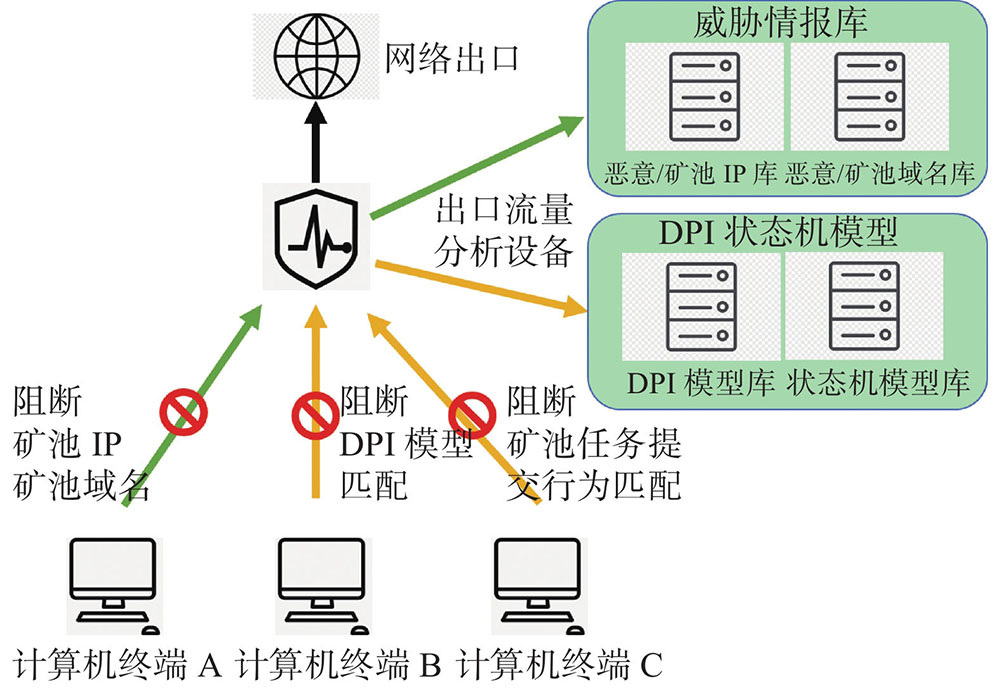
Renting LIU, Yahong ZHENG, Yingmin ZHANG, Mengshu HOU, Chaohui SUN. Detection and Practice of Cryptomining Behavior Based on Deep Packet Inspection[J]. Experiment Science and Technology, 2024, 22(3): 15
Search by keywords or author
- Experiment Science and Technology
- Vol. 22, Issue 3, 15 (2024)
Note: This section is automatically generated by AI . The website and platform operators shall not be liable for any commercial or legal consequences arising from your use of AI generated content on this website. Please be aware of this.
Abstract
Set citation alerts for the article
Please enter your email address


 AI Video Guide
AI Video Guide  AI Picture Guide
AI Picture Guide AI One Sentence
AI One Sentence


